Miktysh Blog.
Your go-to source for everything records management, eDRMS, Office 365, TRIM/Content Manager, RecordPoint, AvePoint, and EncompaaS related.
Categories
Topics
Office 365 Security Concerns – Your Questions Answered
Sep 10, 2019 | Office 365
One of the most common questions we are asked is how secure is Office 365? With so many organisations in regulated industries looking to migrate their content to the cloud so that they can realise the benefits of having a collaborative, modern workspace, it is understandable that many of these organisations have concerns about being able to properly control and secure their information. To address these concerns, we’ve provided a list of answers to the most common Office 365 security concerns our clients raise with us.
1. How is my information protected in Office 365?
Office 365 provides several ways end-users and system administrators can protect and control their information. The most powerful is through Azure Information Protection (AIP) for Office 365. AIP protects information from unauthorised access both internally within an organisation and externally. It does this through the use of security classification labels that are applied to documents and emails. These labels can be applied automatically by system administrators through the rules and conditions they set or manually by end-users or through a combination of the two.
For example, a user could be working on a document that contains a credit card number and when they go to save the document, they are prompted to label the document as ‘confidential’. In this instance this label would have been configured by the system administrator with rules that recognise that the document contained a credit card number which triggered the prompt.
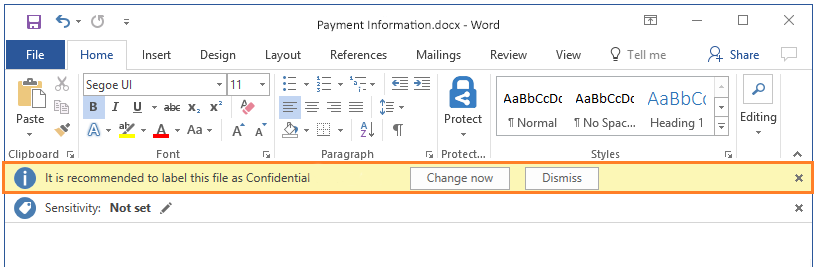
Moreover, you can place further restrictions on content such as not allowing it to be printed or copied, or if it’s an email document preventing it from being forwarded or being able to download attachments.
To apply these further restrictions, Azure Information Protection technology utilises Azure Rights Management (Azure RMS), which integrates with Office 365 to provide content encryption, identity and authorisation control. Using Azure RMS in combination with labels and classifications, system administrators can place specific restrictions on documents by using labels.
For example, a user might be working on a contract, which has the label ‘contract’ applied to it. The user intends to send the contract in an email to a specific person in an external organisation. A restriction can be applied to documents with this label that prevents the recipient of the email from forwarding the email on to anyone else. This means that you can have assurance that only the person who is meant to receive the email will be able to read the contents of the contract. You can also place further restrictions such as time-restrictions that only allow the recipient of the email to view the contract for a specified period of time.
You can see through these examples the endless possible ways in which organisations can secure and control their information in Office 365 using Azure Information Protection. You should note the AIP for Office 365 requires an additional license that (as at the time of writing this) comes to $2.80AUD user/month.
2. Will Office 365 protect my identity?
The majority of security breaches occur when an unauthorised party gains access to a system by stealing a user’s identity. Once access is gained to a ‘low privileged’ user account it becomes easier to access an organisation’s high-value information. This which is why another common Office 365 security concern that is raised with us is what measures Office 365 has in place to protect the identity of its users.
Multi-Factor-Authentication
Office 365 comes with multi factor authentication (MFA), which provides an additional layer of security on top of your usual email and password logins, to verify your identity and prevent unauthorised access. Office 365 provides three different options for MFA. The first is through the Microsoft Authenticator app where after entering their username and password users will receive a push notification on their phone prompting them to enter in a one-time-password (OTP) to login. The second option is to receive a OTP as a text message and third is to receive a phone call on a registered number which will prompt you to enter the hash key to verify your identity and login.

Microsoft also offers more powerful methods of identity protection for Office 365 users through the Azure Active Directory Identity Protection. This comes built in with Office 365 and empowers organisations with the ability to detect suspicious activity that relates to user identity and then configure automated responses to these activities.
Azure Active Directory Identity Protection
Azure Active Directory Identity Protection analyses your Office 365 system configuration to detect key vulnerabilities that could be exploited by a hacker. These include apps that have been unmanaged; multi-factor-authentication not being configured; and having too many ‘privileged users’, such as global administrators who can access valuable Office 365 resources. Azure AD also uses adaptive machine learning techniques to detect six types of risks. These are, users with leaked credentials; sign-ins from anonymous IP addresses; sign-ins from detected devices; sign-ins from IP addresses with suspicious activities; sign-ins from unfamiliar locations and sign-ins from atypical locations.
Your Office 365 system administrator will be able to see reports of any detected risks and vulnerabilities as well as configure settings to respond to these risks all from a centralised dashboard. This dashboard is typically used as a starting point for investigating suspicious activity and determining the steps necessary to remedy it.

With Azure Active Directory Identity Protection, you also have the ability to configure and implement automated responses to suspicious activity. There are three out-of-the-box policies that Microsoft provide for this.
The first is MFA registration policy, which sets a requirement for users to register for MFA. The second is the user risk conditional access policy. The way this works is when Azure AD detects any of the risks that were previously mentioned, it will calculate a probability that the user has been compromised. From there you can configure an automated response to a user’s risk level, such as blocking access to resources or requiring a password change. The last policy is the sign-in policy. This works similarly to the user risk policy, but instead Azure AD assigns a probability of risk that relates to suspicious activity that pertains to a login. From there you can once again assign automated actions based on the different probability levels of risk.
3. What if my data and information is hosted in another country?
Another Office 365 security concern we often hear relates to data sovereignty and where data and information is stored geographically. This is important for data security and privacy as well as for organisations in regulated industries who have region specific compliance obligations that they are required to meet.
By default, your data centre will be picked based on the country of the transaction associated with your initial Office 365 subscription. In Australia, there are two datacentres located in New South Wales and Victoria respectively.
Data sovereignty is a particularly significant problem for organisations with offices located across the globe. To address this problem Microsoft in late 2018 released Office 365 multi-geo, which give organisations with the ability to deploy Exchange Online, OneDrive and SharePoint online across multiple Office 365 datacentres across the globe. This means you no longer need to set up SharePoint, mail servers or file centres on premises in specific regions. Instead you can specify where each user and their data will reside geographically, and easily move existing users and data to different geographically regions from within a single global tenant.
You also have the ability to set security and compliance policies at either a global or regional level. This means organisations have greater control of their information as there are less information silos with all your data and information being housed under a single tenant. This in turn benefits end-users by creating a collaborative, unified workspace where they can securely share and locate information across different geographical regions.
Have more Office 365 security concerns?
Whether you’re a government agency or a private company, if you have any queries on how you can effectively use Office 365 in your organisation while being able to secure and control your information as well as meet your compliance requirements, talk to one of our Office 365 business consultants.

Rick Espin
Business Analyst
Rick is an experienced SharePoint and Office 365 expert. He has helped organisations shift from paper-based records to the Digital Workspace as well as automate critical business processes through the Microsoft Power Platform.
Categories
Topics
Follow us on social
Popular content.

Analytics Driven Information Governance
14.07.2021

The New Normal Requires Zero Trust
27.06.2021

Microsoft 365 Records Management Whitepaper
06.11.2020

Micro Focus Launches Content Manager Select
28.05.2020

Content Manager SharePoint Integration Demo
20.05.2020
Top 7 Hidden Features in Microsoft Teams
11.02.2020

Integrate Content Manager with SharePoint
15.01.2020

Information Management Strategy Example
06.12.2019

How to Approach a Digital Transformation
13.11.2019

Top 5 Benefits of Migrating to Office 365
10.10.2019
Content Manager 9.4 Web Client
19.09.2019
Content Manager 9.4 Sneak Peek – Video Demo
02.09.2019

What Version of SharePoint is on Office 365?
27.06.2019

New SharePoint 2019 Features
08.03.2019

Data Migration Validation Best Practices
08.02.2019

Cloud Governance – RIMPA Queensland Event
27.09.2018
RecordPoint Records365 Demo
09.05.2018

How RecordPoint Enhances Office 365
09.05.2018

6 GDPR Tools to Assist with GDPR Compliance
17.04.2018

Analytics Driven Information Governance
14.07.2021

The New Normal Requires Zero Trust
27.06.2021

Microsoft 365 Records Management Whitepaper
06.11.2020

Micro Focus Launches Content Manager Select
28.05.2020

Content Manager SharePoint Integration Demo
20.05.2020

Top 7 Hidden Features in Microsoft Teams
11.02.2020

Integrate Content Manager with SharePoint
15.01.2020

Information Management Strategy Example
06.12.2019

How to Approach a Digital Transformation
13.11.2019

Top 5 Benefits of Migrating to Office 365
10.10.2019
Content Manager 9.4 Web Client
19.09.2019

Content Manager 9.4 Sneak Peek – Video Demo
02.09.2019

What Version of SharePoint is on Office 365?
27.06.2019

New SharePoint 2019 Features
08.03.2019

Data Migration Validation Best Practices
08.02.2019

Cloud Governance – RIMPA Queensland Event
27.09.2018

RecordPoint Records365 Demo
09.05.2018

How RecordPoint Enhances Office 365
09.05.2018

6 GDPR Tools to Assist with GDPR Compliance
17.04.2018